As some people may know; I like to use the example of “Out of the top 500, how many supercomputers in the world do you think use [your OS here]?”. I use this example for a reason. Unlike conjecture, theories, and even “gut feelings”; it shows that the OS was chosen, and serious money and time were poured into it. This shows that is it at least a player in the field, and can handle the serious levels of computing needed. It also shows things like, tune-ability, flexibility with change, and a few other things that only the people working with their own projects will be able to tell. We are not concerned with that, just that they are on the list; and why if it sticks out as odd to see why.
I am using the TOP500 Project for this information, and it does get re-evaluated often. However, I will say this; just like in nature there will always be a pretty clear delineation when it comes down to who is the “Winner” in this space. Or the most efficient/successful like in nature.
The reason I write this article is to show a certain group of people an example of the difference in reality versus what advertisements, rumors, and self-perception have molded in their minds. I think it is a good exercise to show the affects of the budgets used to change our perceptions. A good example is the budget used by companies like Microsoft (over $2,000,000,000); and Apple (over $1,000,000 in 2013/2014). This is just money, and perception however. This will never affect real life numbers on performance, math doesn’t lie. Results and time are my favorite sources of information. Its a simple concept, there are 1000s of ways to move items. However, in our lives in this age of technology the wheel is still very much in use. Its the best solution at the time…. (a small but powerful statement).
So in lieu of keeping you away from the data pron you came to look at:
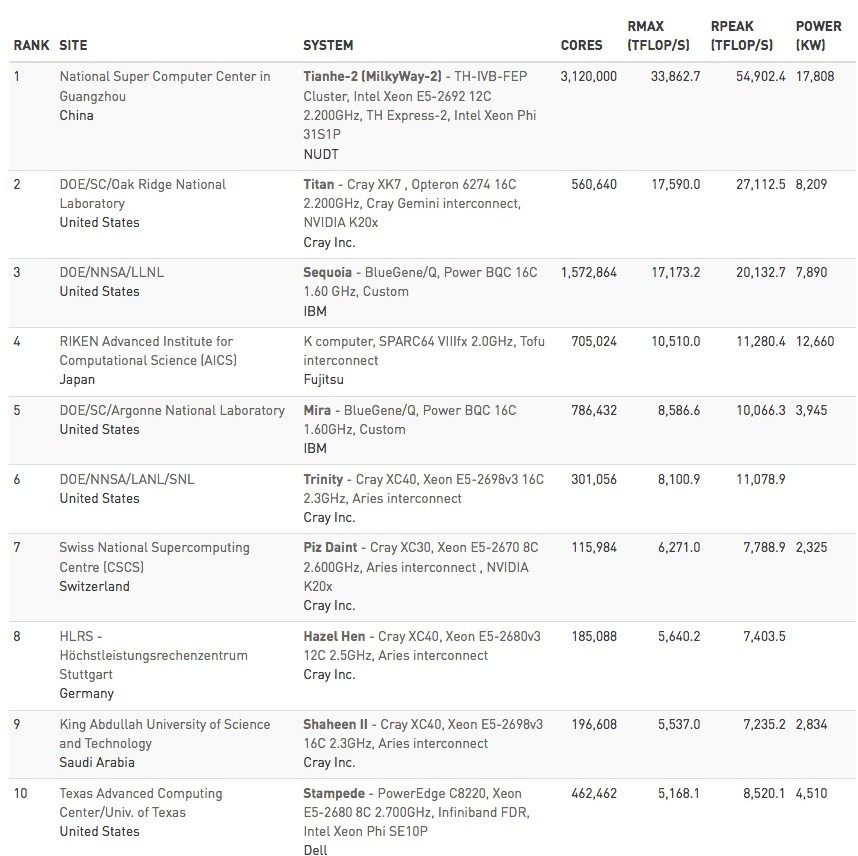
Top 10 Super Super Computers – Nov 2015
Here is the actual breakdown by OS (as of Nov 2015), as I know that is what most people are interested in:
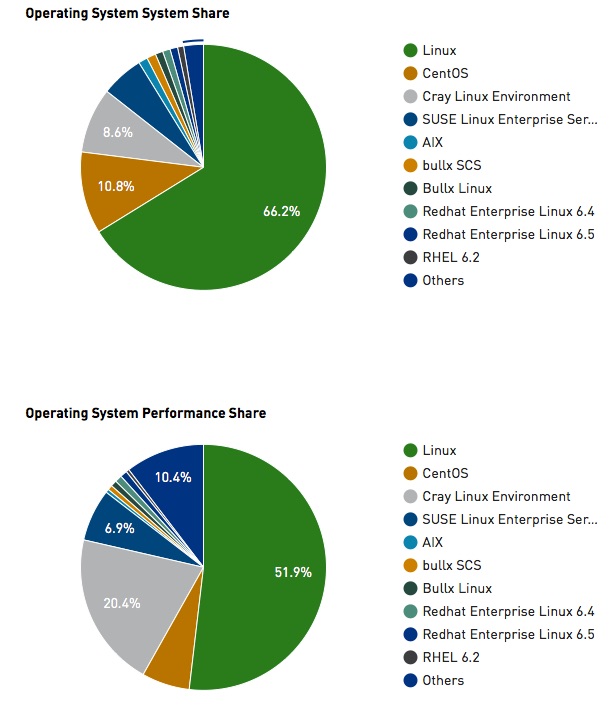
I know some people are wondering where is Windows, or IOS. If you will notice; even in the breakdowns by OS they are pretty much all Linux/BSD [Windows isn’t even a filter option on their site as of right now]. This list is more a list of flavors of Linux with a few BSD machines in the list. You will notice, like in most of the lists done in the past; there is not a single Microsoft product on the list. This is a very simple, and very important fact that way too many people make. This includes everyone from the guy that fixes your desktop all the way up to the VP of Infrastructure. They are all swayed by what they own, and the amount of advertising spewed forth at them non-stop. Keep in mind these people are generally more connected than the rest of the populous. Thus, affected even more so by the ads. Combine that with sales people/calls/pressures on support/etc, and you get smart companies ( I didn’t say large), that make really bad technology decisions. I exclude myself from that ad loop; and look purely at statistical performance. This is great for business; since you can eliminate a TON of costs; and licensing fees/etc that you would have if you went with something not on this list.
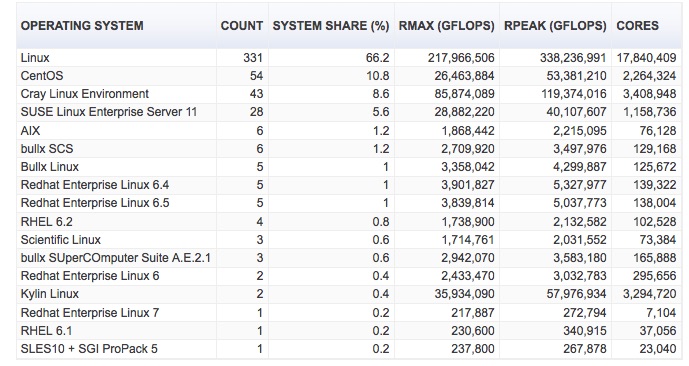
Want to see the full list of over 500 super computers for 2015?
 Notice it is yellow
Notice it is yellow







